-
Written By Danish
-
Updated on January 11th, 2021
Protect against Ransomware Attack to Save Your Data
Over the past few years, Ransomware has been one of the topmost cyber security threats or cyber extortion for the computer users. On 12th May 2017, it was reported that Ransomware attack has infected more than 230,000 computers in over 150 countries including the United Kingdom. This worldwide cyber attack, named WannaCry Ransomware attack, was done by the WannaCry Ransomware cryptoworm. In this article, I’ll describe Ransomware and its harmful effects. Also, I’ll show you how to protect against Ransomware and how to recover your invaluable data after Ransomware attack.
What is Ransomware Attack?
In simple terms, Ransomware is a type of malicious software that can easily block access to your computer system until you pay a sum of money as ransom. Though Ransomware usually aims at individuals, business is also targetted nowadays. The Ransomware virus helps the cyber criminals to perform data kidnapping and lock-screen attacks with ease. In data kidnapping, the malware encrypts the files on an infected device as well as on other devices connected to the network. In lock-screen attack, the malware changes the login credentials for a computing device.
If the Ransomware virus is normal, it may lock your computer system. Luckily, it’s not that difficult for any knowledgeable person to unlock the system. But advanced Ransomware virus uses cryptoviral extortion technique that can encrypt your files in order to make them inaccessible. To decrypt the files infected by Ransomware attack, you need to pay a ransom.
The only motive behind Ransomware attack is to get a sum of money from the victims. Unlike other types of attack, it notifies the victims about the exploit. Also, the victims get instructions on how to recover from Ransomware attack. The cyber criminals demand ransom in the form of virtual money like Bitcoin so they can protect their real identity. Ransomware has become a rising trend among cyber criminals these days who look for a quick payout.
How do you get Ransomware virus?
Infected software apps, infected external storage devices, malicious email attachments, etc. are the best possible sources from where Ransomware virus comes into your PC. Also, it can come when you visit some compromised websites which have malicious code embedded in them. Genrally, the cyber criminals who have little or almost no prior expertise, use RaaS (Ransomware-as-a-Service). This program helps them execute the cyber attack with very little effort. To extort ransom from their victims, they use following approaches:
- First, the cyber criminals encrypt files on an infected computer system. And then, they sell a product (commercialware) that actually promises to help the victim unlock or decrypt files. Also, it promises to prevent future malware attacks.
- They send a pop-up message or email warning that if the victim doesn’t pay the ransom by a certain date, they’ll destroy the private key. The private key is required to unlock the infected device or decrypt the encrypted files.
- They deceive victims by telling them that they’re subject to an official inquiry. They inform that some illegal web content or unlicensed software has been found on their computer. After that, they give instructions to the victims for how to pay the fine (which is actually ransom).
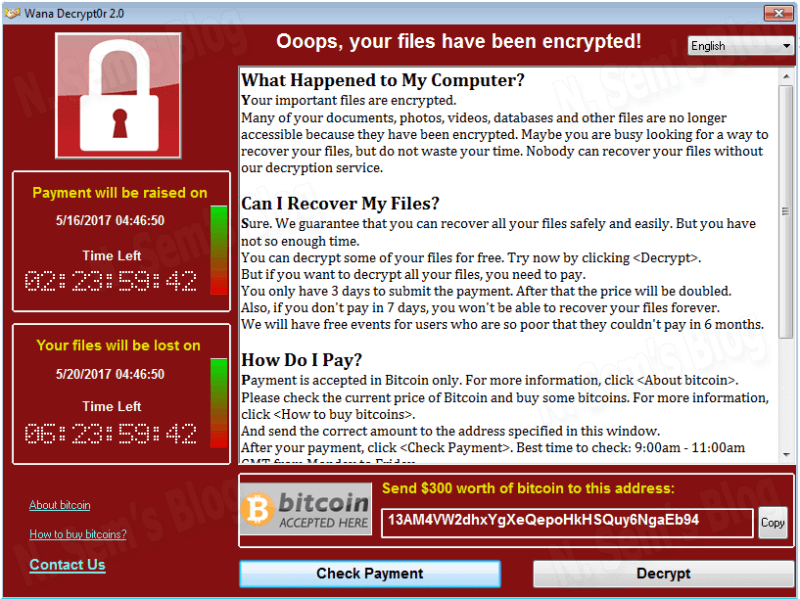
WannaCry Ransomware Attack
On 12th May 2017, the world has witnessed the most severe and massive cyber attack of all time, known as WannaCry Ransomware attack. In just one day, it affected more than 200,000 organizations in over 150 countries around the world. This cyber attack targetted computers running the Windows-based operating systems.
Protect Against Ransomware Attacks
The best way to protect against Ransomware attack and other types of cyber extortion is taking backup of your computer system on a regular basis. Also, update the software applications including Antivirus program regularly.
Things to remember
- Being an end-user, you should not click the links in email messages received from the strangers or an unknown source. Also, you should not open any email attachments.
- Don’t visit compromised websites which have malicious code or scripts embedded in them. Make sure you’re using an Internet security program like Norton Internet Security. It can successfully detect bad software from malicious websites and drive-by downloads. Also, it warns you when you try to visit a malicious website.
Avoid Ransomware Attack
Ransomware attack are nearly inevitable. Make sure you do everything to avoid paying the ransom to cyber criminals. Every individuals and organization should take corrective measures for data protection to ensure that damage is minimal. In such a situation, you can perform maximum possible recovery in a quick time as possible. Make the following strategies:
- Categorize the authentication systems and domains;
- Keep the storage snapshots up-to-date outside the main storage pool;
- Put extremely hard restrictions, like who can access data, what data he/she can access and when to access.
Precaution You Should Take After Ransomware Attack
If you’ve just faced a Ransomware attack on your computer system, kindly take the following precautions:
- Disconnect the computer system at once from the Internet or network.
- Neither update nor run any Antivirus program on your computer system.
- And most importantly, shut down the computer system by using the Power button.
- Create a copy of your infected disk or the files for later analysis. You may need this for decryption of files.
- Try to boot your computer system into safe mode. After that, run the Antivirus program for the deep scan. This trick may help you disinfect your computer system. Although the chances are very low, there’s no harm in trying.
- Try to identify the Ransomware virus which has infected your computer system. You can use a free online service ID Ransomware. If it works for you, now check if a Ransomware Decrypt tool is available for your Ransomware virus.
Data Recovery After Ransomware Attack
Though there’s no possible way to recover files infected by Ransomware attack, still you can try some smart data recovery tools. Since there’s no way to detect the level of infection caused by Ransomware attack, you must hit a shot in the dark. And that’s only possible if you use a data recovery tool. You should download the free demo version of Removable Media Recovery software to recover files from the infected system. But make sure you install this software on a new fresh computer system. Once you complete the installation process, connect the infected disk as a removable storage media with the help of SATA Hard Drive Connector. Now you can see the infected disk as the removable media. After that, launch Removable Media Recovery software on your system to perform data recovery from the infect disk.
Watch the online video tutorial below
About The Author:
Related Post